Pessimism of the Intellect, Optimism of the Will Favorite posts | Manifold podcast | Twitter: @hsu_steve
Tuesday, March 28, 2017
The brute tyranny of g-loading: Lawrence Krauss and Joe Rogan
I love Joe Rogan -- he has an open, inquisitive mind and is a sharp observer of life and human society. See, for example, this interview with Dan Bilzerian about special forces, professional poker, sex, drugs, heart attacks, life, happiness, hedonic treadmill, social media, girls, fame, prostitution, money, steroids, stem cell therapy, and plenty more.
I know Lawrence Krauss quite well -- he and I work in the same area of theoretical physics. However, the 20+ minute opening segment in which Krauss tries to explain gauge symmetry (1, 2, 3) to Joe is downright painful. Some things are just conceptually hard, and are built up from other concepts that are themselves non-obvious.
Gauge symmetry is indeed central to modern theoretical physics -- all of the known forces of nature are gauge interactions. I've been at an uncountable number of cocktail parties (sometimes with other professors) where I've tried to explain this concept to someone as sincerely interested as Rogan is in the video. Who doesn't like to hear about fundamental laws of Nature and deep principles of physical reality?
No matter how clearly a very g-loaded concept is explained, it is challenging for the typical person to comprehend. (This is almost a definition.) Many ideas in physics are challenging even to college professors. One sad aspect of the Internet is that there isn't any significant discussion forum or blog comment section where even much simpler concepts such as regression to the mean are understood by all the participants.
Listening to the conversation between Joe and Lawrence about gauge theory and the Higgs field, I couldn't help but think of this Far Side cartoon:
Oppenheimer: Mathematics is "an immense enlargement of language, an ability to talk about things which in words would be simply inaccessible."
See also this Reddit discussion of the podcast episode.
Just Like Heaven
Musical intermission. Choose your favorite!
For me it's not the same without that 80's synth...
For me it's not the same without that 80's synth...
Saturday, March 25, 2017
Robots Proctor Online Exams
For background on this subject, see How to beat online exam proctoring. It is easy for clever students to beat existing security systems for online exams. Enterprising students could even set up "cheating rooms" that make it easy for test takers to cheat. Judging by the amount of traffic this old post gets, cheating on online exams is a serious problem.
Machine learning to the rescue! :-) The machines don't have to be 100% accurate in detection -- they can merely flag suspicious moments in the data and ask a human proctor to look more carefully. This makes the overall system much more scalable.
The monitoring data (e.g., video from webcam + pov cam) from a particular exam could potentially be stored forever. In an extreme case, a potential employer who wants to be sure that Johnny passed the Python coding (or psychometric g) exam for real could be granted access to the stored data by Johnny, to see for themselves.
Automated Online Exam ProctoringThis work is related to the issued patent
Atoum, Chen, Liu, Hsu, and Liu
IEEE Transactions on Multimedia
Abstract:
Massive open online courses (MOOCs) and other forms of remote education continue to increase in popularity and reach. The ability to efficiently proctor remote online examinations is an important limiting factor to the scalability of this next stage in education. Presently, human proctoring is the most common approach of evaluation, by either requiring the test taker to visit an examination center, or by monitoring them visually and acoustically during exams via a webcam. However, such methods are labor-intensive and costly. In this paper, we present a multimedia analytics system that performs automatic online exam proctoring. The system hardware includes one webcam, one wearcam, and a microphone, for the purpose of monitoring the visual and acoustic environment of the testing location. The system includes six basic components that continuously estimate the key behavior cues: user verification, text detection, voice detection, active window detection, gaze estimation and phone detection. By combining the continuous estimation components, and applying a temporal sliding window, we design higher level features to classify whether the test taker is cheating at any moment during the exam. To evaluate our proposed system, we collect multimedia (audio and visual) data from 24 subjects performing various types of cheating while taking online exams. Extensive experimental results demonstrate the accuracy, robustness, and efficiency of our online exam proctoring system.
Online examination proctoring system
WO 2014130769 A1
ABSTRACT
The system to proctor an examination includes a first camera (10) worn by the examination taking subject (12) and directed to capture images in subject's field of vision. A second camera (14) is positioned to record an image of the subject's face during the examination. A microphone (26) captures sounds within the room, which are analyzed to detect speech utterances. The computer system (8) is programmed to store captured images from said first camera. The computer (16) is also programmed to issue prompting events instructing the subject to look in a direction specified by the computer at event intervals not disclosed to subject in advance and to index for analysis the captured images in association with indicia corresponding to the prompting events.
Publication number WO2014130769 A1
Publication type Application
Application number PCT/US2014/017584
Publication date Aug 28, 2014
Filing date Feb 21, 2014
Priority date Feb 25, 2013
Also published as US9154748, US20140240507
Inventors Stephen Hsu, Xiaoming Liu, Xiangyang Alexander LIU
Applicant Board Of Trustees Of Michigan State University
Thursday, March 23, 2017
The weirdest academic seminar ever
... but in a good way! :-)
Beijing-based economist and rapper Andrew Dougherty ("Big Daddy Dough") presents The Redprint: Rhyme and Reason in the Riddle Kingdom at the BYU Kennedy Center.
This is his classic cover Beijing State of Mind:
Dougherty interview on Sinica podcast.
Beijing-based economist and rapper Andrew Dougherty ("Big Daddy Dough") presents The Redprint: Rhyme and Reason in the Riddle Kingdom at the BYU Kennedy Center.
This is his classic cover Beijing State of Mind:
Dougherty interview on Sinica podcast.
With Kasparov in NYC
We were together on a panel talking about AI. I challenged him to a quick game of blitz but he declined ;-) The moderator is Josh Wolfe of Lux Capital.
More Kasparov on this blog.
Nunes, Trump, Obama and Who Watches the Watchers?
I've made this separate entry from the update to my earlier discussion FISA, EO 12333, Bulk Collection, and All That. I believe the Nunes revelations from yesterday support my contention that the Trump team intercepts are largely "incidental" collections (e.g., bulk collections using tapped fiber, etc.) under 12333, and the existence of many (leaked) intel reports featuring these intercepts is likely a consequence of Obama's relaxation of the rules governing access to this bulk data. At least, the large number of possible leakers helps hide the identities of the actual leakers!
EO12333 + Obama OKs unprecedented sharing of this info as he leaves office = recent leaks? Note the use of the term "incidentally" and the wide dissemination (thanks to Obama policy change as he left office).
WSJ: ... “I recently confirmed that on numerous occasions the intelligence community incidentally collected information about U.S. citizens involved in the Trump transition,” Mr. Nunes said, reading a brief statement to reporters on Capitol Hill on Wednesday afternoon. “Details about U.S. persons associated with the incoming administration—details with little or no apparent foreign intelligence value—were widely disseminated in intelligence community reporting.”The change put in place as Obama left office is probably behind the large number of circulating reports that feature "incidentally" captured communications of the Trump team. The NYTimes article below is from February.
... Mr. Nunes added that it was “possible” the president himself had some of his communication intercepted, and has asked the Federal Bureau of Investigation, National Security Agency and other intelligence agencies for more information.
NYTimes: ... Until now, National Security Agency analysts have filtered the surveillance information for the rest of the government. They search and evaluate the information and pass only the portions of phone calls or email that they decide is pertinent on to colleagues at the Central Intelligence Agency, the Federal Bureau of Investigation and other agencies. And before doing so, the N.S.A. takes steps to mask the names and any irrelevant information about innocent Americans.It appears that the number of individuals allowed to search bulk, incidentally collected data has been enlarged significantly. Who watches these watchers? (There must now be many thousands...)
[ So FBI is only getting access to this data for the first time. It is interesting that Nunes said that NSA would comply with his request for more information but that FBI has not complied. It seems possible that FBI does not yet have good internal controls over how its agents use these new privileges. ]
The new system would permit analysts at other intelligence agencies to obtain direct access to raw information from the N.S.A.’s surveillance to evaluate for themselves. If they pull out phone calls or email to use for their own agency’s work, they would apply the privacy protections masking innocent Americans’ information — a process known as “minimization” — at that stage, Mr. Litt said.
... FISA covers a narrow band of surveillance: the collection of domestic or international communications from a wire on American soil, leaving most of what the N.S.A. does uncovered. In the absence of statutory regulation, the agency’s other surveillance programs are governed by rules the White House sets under a Reagan-era directive called Executive Order 12333.
... [it is unclear what] rules say about searching the raw data using names or keywords intended to bring up Americans’ phone calls or email that the security agency gathered “incidentally” under the 12333 surveillance programs ...
Sophos: Obama administration signs off on wider data-sharing for NSA ... Patrick Toomey, a lawyer for the American Civil Liberties Union (ACLU), put it in an interview with the New York Times, 17 intelligence agencies are now going to be “rooting… through Americans’ emails with family members, friends and colleagues, all without ever obtaining a warrant”.Added: Quick and dirty summary of new rules governing access to raw SIGINT. Note, lots of room for abuse in what I quote below:
The new rules mean that the FBI, the CIA, the DEA, and intelligence agencies of the US military’s branches and more, will be able to search through raw signals intelligence (SIGINT): intercepted signals that include all manner of people’s communications, be it via satellite transmissions, phone calls and emails that cross network switches abroad, as well as messages between people abroad that cross domestic network switches.
Section III: ... NSA may make raw SIGINT available through its own systems, through a shared IC or other government capability (like a cloud environment), or by transferring the information to the IC element's information systems.Here are the entities who now have access (thanks Obama!) to raw SIGINT, and seem to have the discretionary power to "unmask" US citizens appearing in the data.
Section V: ... Communications solely between U.S. persons “inadvertently retrieved during the selection of foreign communications” will be destroyed except if they contain significant foreign intelligence or counterintelligence as determined by the IC element.
Section VI: ... An IC element may disseminate U.S. person information "derived solely from raw SIGINT" under these procedures ... if ... the information is “necessary to understand the foreign intelligence or counterintelligence information,”
IC elements are defined under 3.5(h) of E.O. 12333 as: (1) The Office of the Director of National Intelligence; (2) The Central Intelligence Agency; (3) The National Security Agency; (4) The Defense Intelligence Agency; (5) The National Geospatial-Intelligence Agency; (6) The National Reconnaissance Office; (7) The other offices within the Department of Defense for the collection of specialized national foreign intelligence through reconnaissance programs; (8) The intelligence and counterintelligence elements of the Army, the Navy, the Air Force, and the Marine Corps; (9) The intelligence elements of the Federal Bureau of Investigation; (10) The Office of National Security Intelligence of the Drug Enforcement Administration; (11) The Office of Intelligence and Counterintelligence of the Department of Energy; (12) The Bureau of Intelligence and Research of the Department of State; (13) The Office of Intelligence and Analysis of the Department of the Treasury; (14) The Office of Intelligence and Analysis of the Department of Homeland Security; (15) The intelligence and counterintelligence elements of the Coast Guard; and (16) Such other elements of any department or agency as may be designated by the President, or designated jointly by the Director and the head of the department or agency concerned, as an element of the Intelligence Community.
Tuesday, March 21, 2017
FISA, EO 12333, Bulk Collection, and All That
Some basic questions for the experts:
1. To what extent does EO12333 allow surveillance of US individuals without FISA warrant?
2. To what extent are US voice conversations recorded via bulk collection (and preserved for, e.g., 5 or more years)? The email answer is clear ... But now automated voice recognition and transcription make storage of voice conversations much more scalable.
3. To what extent do Five Eyes intel collaborators have direct access to preserved data?
4. Are "experts" and media pundits and Senators even asking the right questions on this topic? For example, can stored bulk-collected voice data from a US individual be accessed by NSA without FISA approval by invoking 12333? How can one prevent a search query on stored data from producing results of this type?
See, e.g., Overseas Surveillance in an Interconnected World (Brennan Center for Justice at NYU School of Law), ACLU.org, and Executive Order 12333 (epic.org):
EPIC has tracked the government's reliance on EO 12333, particularly the reliance on Section 1:12(b)(13), which authorizes the NSA to provide "such administrative and technical support activities within and outside the United States as are necessary to perform the functions described in sections (1) through (12) above, including procurement." This provision appears to have opened the door for the NSA's broad and unwarranted surveillance of U.S. and foreign citizens.Tye in the WaPo:
Executive Order 12333 was signed by President Ronald Reagan on December 4, 1981. It established broad new surveillance authorities for the intelligence community, outside the scope of public law. EO 12333 has been amended three times. It was amended by EO 13284 on January 23, 2003 and was then amended by EO 13555 on August 27, 2004. EO 13555 was subtitled "Strengthened Management of the Intelligence Community" and reflected the fact that the Director of National Intelligence (DNI) now existed as the head of the intelligence community, rather than the CIA which had previously served as the titular head of the IC. EO 13555 partially supplemented and superseded EO 12333. On July 30, 2008, President George W. Bush signed EO 13470, which further supplemented and superseded EO 12333 to strengthen the role of the Director of National Intelligence.
Since the Snowden revaluations there has been a great deal of discussion regarding the activities of the IC community, but relatively little attention has been paid to EO 12333. EO 12333 often serves an alternate basis of authority for surveillance activities, above and beyond Section 215 and 702. As Bruce Schneier has emphasized, "Be careful when someone from the intelligence community uses the caveat "not under this program," or "not under this authority"; almost certainly it means that whatever it is they're denying is done under some other program or authority. So when[NSA General Counsel Raj] De said that companies knew about NSA collection under Section 702, it doesn't mean they knew about the other collection programs." Senator Dianne Feinstein (D-CA), Chair of the Senate Intelligence Committee, has said in August 2013 that, "The committee does not receive the same number of official reports on other NSA surveillance activities directed abroad that are conducted pursuant to legal authorities outside of FISA (specifically Executive Order 12333), but I intend to add to the committee's focus on those activities." In July 2014, a former Obama State Department official, John Napier Tye, wrote an Op-Ed in the Washington Post calling for greater scrutiny of EO 12333. Tye noted that "based in part on classified facts that I am prohibited by law from publishing, I believe that Americans should be even more concerned about the collection and storage of their communications under Executive Order 12333 than under Section 215."
... [EO 12333] authorizes collection of the content of communications, not just metadata, even for U.S. persons. Such persons cannot be individually targeted under 12333 without a court order. However, if the contents of a U.S. person’s communications are “incidentally” collected (an NSA term of art) in the course of a lawful overseas foreign intelligence investigation, then Section 2.3(c) of the executive order explicitly authorizes their retention. It does not require that the affected U.S. persons be suspected of wrongdoing and places no limits on the volume of communications by U.S. persons that may be collected and retained.See also Mining your data at NSA (source of image at top).
[ E.g., NSA could "incidentally" retain the email of a US individual which happens to be mirrored in Google or Yahoo data centers outside the US, as part of bulk collection for an ongoing (never ending) foreign intelligence or anti-terrorism investigation... ]
“Incidental” collection may sound insignificant, but it is a legal loophole that can be stretched very wide. Remember that the NSA is building a data center in Utah five times the size of the U.S. Capitol building, with its own power plant that will reportedly burn $40 million a year in electricity.
UPDATE: EO12333 + Obama OKs unprecedented sharing of this info as he leaves office = recent leaks? Note the use of the term "incidentally" and the wide dissemination (thanks to Obama policy change as he left office).
WSJ: ... “I recently confirmed that on numerous occasions the intelligence community incidentally collected information about U.S. citizens involved in the Trump transition,” Mr. Nunes said, reading a brief statement to reporters on Capitol Hill on Wednesday afternoon. “Details about U.S. persons associated with the incoming administration—details with little or no apparent foreign intelligence value—were widely disseminated in intelligence community reporting.”
... Mr. Nunes added that it was “possible” the president himself had some of his communication intercepted, and has asked the Federal Bureau of Investigation, National Security Agency and other intelligence agencies for more information.
The change put in place as Obama left office is probably behind the large number of circulating reports that feature "incidentally" captured communications of the Trump team. The NYTimes article below is from February.
NYTimes: ... Until now, National Security Agency analysts have filtered the surveillance information for the rest of the government. They search and evaluate the information and pass only the portions of phone calls or email that they decide is pertinent on to colleagues at the Central Intelligence Agency, the Federal Bureau of Investigation and other agencies. And before doing so, the N.S.A. takes steps to mask the names and any irrelevant information about innocent Americans.It appears that the number of individuals allowed to search bulk, incidentally collected data has been enlarged significantly. Who watches these watchers? (There must now be many thousands...)
The new system would permit analysts at other intelligence agencies to obtain direct access to raw information from the N.S.A.’s surveillance to evaluate for themselves. If they pull out phone calls or email to use for their own agency’s work, they would apply the privacy protections masking innocent Americans’ information — a process known as “minimization” — at that stage, Mr. Litt said.
... FISA covers a narrow band of surveillance: the collection of domestic or international communications from a wire on American soil, leaving most of what the N.S.A. does uncovered. In the absence of statutory regulation, the agency’s other surveillance programs are governed by rules the White House sets under a Reagan-era directive called Executive Order 12333.
... [it is unclear what] rules say about searching the raw data using names or keywords intended to bring up Americans’ phone calls or email that the security agency gathered “incidentally” under the 12333 surveillance programs ...
Sophos: ... Patrick Toomey, a lawyer for the American Civil Liberties Union (ACLU), put it in an interview with the New York Times, 17 intelligence agencies are now going to be “rooting… through Americans’ emails with family members, friends and colleagues, all without ever obtaining a warrant”.
The new rules mean that the FBI, the CIA, the DEA, and intelligence agencies of the US military’s branches and more, will be able to search through raw signals intelligence (SIGINT): intercepted signals that include all manner of people’s communications, be it via satellite transmissions, phone calls and emails that cross network switches abroad, as well as messages between people abroad that cross domestic network switches.
Monday, March 20, 2017
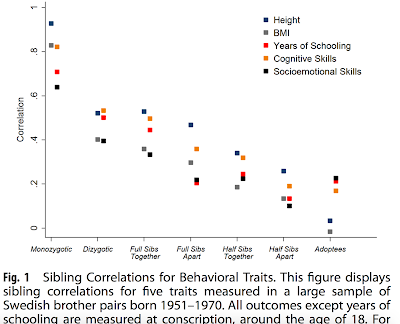
Everything is Heritable
The figure above comes from the paper below. A quick glance shows that for pairs of individuals: 1. Increasing genetic similarity implies increasing trait similarity (for traits including height, cognitive ability, years of education) 2. Home environments (raised Together vs Apart; Adoptees) have limited impact on the trait (at least in relatively egalitarian Sweden).
It's all here in one simple figure, but still beyond the grasp of most people struggling to understand how humans and human society work... See also The Mystery of Non-Shared Environment.
Genetics and educational attainment
David Cesarini & Peter M. Visscher
NPJ Science of Learning 2, Article number: 4 (2017)
doi:10.1038/s41539-017-0005-6
Abstract: We explore how advances in our understanding of the genetics of complex traits such as educational attainment could constructively be leveraged to advance research on education and learning. We discuss concepts and misconceptions about genetic findings with regard to causes, consequences, and policy. Our main thesis is that educational attainment as a measure that varies between individuals in a population can be subject to exactly the same experimental biological designs as other outcomes, for example, those studied in epidemiology and medical sciences, and the same caveats about interpretation and implication apply.
Wednesday, March 15, 2017
Ginormous Neural Nets and Networks of Networks
Now that we have neural nets that are good at certain narrow tasks, such as image or speech recognition, playing specific games, translating language, ... the next stage of development will involve 1. linking these specialized nets together in a more general architecture ("Mixtures of Experts"), and 2. generalizing what is learned in one class of problems to different situations ("transfer learning"). The first paper below is by Google Brain researchers and the second from Google DeepMind.
See also A Brief History of the Future, as told to the Masters of the Universe.
See also A Brief History of the Future, as told to the Masters of the Universe.
Outrageously Large Neural Networks: The Sparsely-Gated Mixture-of-Experts Layer
Noam Shazeer, Azalia Mirhoseini, Krzysztof Maziarz, Andy Davis, Quoc Le, Geoffrey Hinton, Jeff Dean
(Submitted on 23 Jan 2017)
The capacity of a neural network to absorb information is limited by its number of parameters. Conditional computation, where parts of the network are active on a per-example basis, has been proposed in theory as a way of dramatically increasing model capacity without a proportional increase in computation. In practice, however, there are significant algorithmic and performance challenges. In this work, we address these challenges and finally realize the promise of conditional computation, achieving greater than 1000x improvements in model capacity with only minor losses in computational efficiency on modern GPU clusters. We introduce a Sparsely-Gated Mixture-of-Experts layer (MoE), consisting of up to thousands of feed-forward sub-networks. A trainable gating network determines a sparse combination of these experts to use for each example. We apply the MoE to the tasks of language modeling and machine translation, where model capacity is critical for absorbing the vast quantities of knowledge available in the training corpora. We present model architectures in which a MoE with up to 137 billion parameters is applied convolutionally between stacked LSTM layers. On large language modeling and machine translation benchmarks, these models achieve significantly better results than state-of-the-art at lower computational cost.
PathNet: Evolution Channels Gradient Descent in Super Neural NetworksThe figure below describes the speedup in learning new games based on previous learning from playing a game of different type.
Chrisantha Fernando, Dylan Banarse, Charles Blundell, Yori Zwols, David Ha, Andrei A. Rusu, Alexander Pritzel, Daan Wierstra (Submitted on 30 Jan 2017)
For artificial general intelligence (AGI) it would be efficient if multiple users trained the same giant neural network, permitting parameter reuse, without catastrophic forgetting. PathNet is a first step in this direction. It is a neural network algorithm that uses agents embedded in the neural network whose task is to discover which parts of the network to re-use for new tasks. Agents are pathways (views) through the network which determine the subset of parameters that are used and updated by the forwards and backwards passes of the backpropogation algorithm. During learning, a tournament selection genetic algorithm is used to select pathways through the neural network for replication and mutation. Pathway fitness is the performance of that pathway measured according to a cost function. We demonstrate successful transfer learning; fixing the parameters along a path learned on task A and re-evolving a new population of paths for task B, allows task B to be learned faster than it could be learned from scratch or after fine-tuning. Paths evolved on task B re-use parts of the optimal path evolved on task A. Positive transfer was demonstrated for binary MNIST, CIFAR, and SVHN supervised learning classification tasks, and a set of Atari and Labyrinth reinforcement learning tasks, suggesting PathNets have general applicability for neural network training. Finally, PathNet also significantly improves the robustness to hyperparameter choices of a parallel asynchronous reinforcement learning algorithm (A3C).
Sunday, March 12, 2017
Dalton Conley: The Bell Curve Revisited and The Genome Factor
Dalton Conley is the Henry Putnam University Professor of Sociology at Princeton University. He is unique in having earned a second PhD in behavior genetics after his first in Sociology.
In the talk and paper below he discusses molecular genetic tests of three hypotheses from Herrnstein and Murray's The Bell Curve: Intelligence and Class Structure in American Life. This much vilified book is indeed about intelligence and class structure, but almost entirely not about race. Racial differences in intelligence are only discussed in one chapter, and the authors do not make strong claims as to whether the causes for these differences are genetic or environmental. (They do leave open the possibility of a genetic cause for part of the gap, which has led to all kinds of trouble for the surviving author, Charles Murray.) The three questions addressed by Dalton do not involve race.
Harvard professor Harvey Mansfield organized a panel to commemorate the 20th anniversary of The Bell Curve back in 2014. You can find the video here.
1. How is it that the "core propositions" of The Bell Curve can be discussed in a paper published in Sociological Science and at an advanced seminar at Princeton, but Charles Murray is not allowed to speak at Middlebury College?
2. There must be many social scientists or academics in the humanities (or undergraduates at Middlebury) with strong opinions about The Bell Curve, despite never having read it, and despite having a completely erroneous understanding of what the book is about. If you are one of these people, shouldn't you feel embarrassed or ashamed?
See also Conley's new book Genome Factor: What the Social Genomics Revolution Reveals about Ourselves, Our History, and the Future.
Conley, Steve Pinker, and I were on a 92nd Street Y panel together in 2016.
In the talk and paper below he discusses molecular genetic tests of three hypotheses from Herrnstein and Murray's The Bell Curve: Intelligence and Class Structure in American Life. This much vilified book is indeed about intelligence and class structure, but almost entirely not about race. Racial differences in intelligence are only discussed in one chapter, and the authors do not make strong claims as to whether the causes for these differences are genetic or environmental. (They do leave open the possibility of a genetic cause for part of the gap, which has led to all kinds of trouble for the surviving author, Charles Murray.) The three questions addressed by Dalton do not involve race.
Harvard professor Harvey Mansfield organized a panel to commemorate the 20th anniversary of The Bell Curve back in 2014. You can find the video here.
1. How is it that the "core propositions" of The Bell Curve can be discussed in a paper published in Sociological Science and at an advanced seminar at Princeton, but Charles Murray is not allowed to speak at Middlebury College?
2. There must be many social scientists or academics in the humanities (or undergraduates at Middlebury) with strong opinions about The Bell Curve, despite never having read it, and despite having a completely erroneous understanding of what the book is about. If you are one of these people, shouldn't you feel embarrassed or ashamed?
The Bell Curve Revisited: Testing Controversial Hypotheses with Molecular Genetic DataWhile I find the work described above to be commendable (i.e., it foreshadows how molecular genetic methods will eventually address even the most complex and controversial topics in social science), I don't feel that the conclusions reached are beyond question. For example, see this worthwhile comment at the journal web page:
Dalton Conley, Benjamin Domingue
Sociological Science, July 5, 2016
DOI 10.15195/v3.a23
In 1994, the publication of Herrnstein’s and Murray’s The Bell Curve resulted in a social science maelstrom of responses. In the present study, we argue that Herrnstein’s and Murray’s assertions were made prematurely, on their own terms, given the lack of data available to test the role of genotype in the dynamics of achievement and attainment in U.S. society. Today, however, the scientific community has access to at least one dataset that is nationally representative and has genome-wide molecular markers. We deploy those data from the Health and Retirement Study in order to test the core series of propositions offered by Herrnstein and Murray in 1994. First, we ask whether the effect of genotype is increasing in predictive power across birth cohorts in the middle twentieth century. Second, we ask whether assortative mating on relevant genotypes is increasing across the same time period. Finally, we ask whether educational genotypes are increasingly predictive of fertility (number ever born [NEB]) in tandem with the rising (negative) association of educational outcomes and NEB. The answers to these questions are mostly no; while molecular genetic markers can predict educational attainment, we find little evidence for the proposition that we are becoming increasingly genetically stratified.
This is a fascinating study! My comments below pertain to Proposition #1, that “The effect of genetic endowment is increasing over time with the rise of a meritocratic society”.Regarding fertility and dysgenic trends, see this more recent paper from the DeCode collaboration in Iceland, which reaches much stronger conclusions in agreement with H&M.
The data reported here do not seem to unequivocally contravene H&M’s hypothesis. The authors focus on the interaction terms, PGS x Birth Year (i.e. cohort), and show that interaction coefficient is slightly negative (b=-0.006, p=0.47), indicating a weakening of the association between genetic endowment and educational attainment, broadly conceived. The finding is that PGSs (polygenic scores) are (slightly) less predictive of educational attainment in later cohorts.
This isn’t that surprising, given educational inflation – over time, higher percentages of the population achieve any given level of educational attainment. In addition, as shown in Table 3 and mentioned in the Discussion section, this decline in importance of genetic endowment is restricted only to the ‘lower half of the educational distribution’. In contrast, genetic endowment (measured by PGSs) has become even more important across cohorts in predicting the ‘transition from a completed college degree to graduate education’ (534). Isn’t this what we’d expect to happen as the level of educational attainment at the lower half of the distribution becomes increasingly decoupled from cognitive ability?
H&M argued that cognitive ability is becoming more important in determining one’s life chances. The authors of this paper don’t actually test this hypothesis. They instead create polygenic scores *of educational attainment* (!) rather than cognitive ability – based on the GWAS of Rietveld et al. (2013) – and find that genetic predictors of *educational attainment* become (slightly) less predictive of educational attainment, on average, i.e. for high school and college. But again, they also report that the association of this genetic correlate (of educational attainment) and educational attainment has actually become stronger for transitions into graduate and professional schools from college.
If I’m not mistaken, the association between cognitive ability (as measured say by standardized tests, SAT, ACT, GRE, AFQT and NEA reports on reading and math ability) and educational attainment has weakened over time. It is possible that cognitive ability is becoming increasingly salient in determining SES as H&M maintain, and at the same time, educational attainment is becoming less salient, simply because the relationship between cognitive ability and educational attainment is becoming weaker. In other words, educational attainment, at least at the lower levels, is less salient in determining relative status. ...
See also Conley's new book Genome Factor: What the Social Genomics Revolution Reveals about Ourselves, Our History, and the Future.
Conley, Steve Pinker, and I were on a 92nd Street Y panel together in 2016.
Wednesday, March 08, 2017
"We need to encourage real diversity of thought in the professoriate"
John Etchemendy is a former Provost of Stanford University.
The Threat From WithinSee also
... Over the years, I have watched a growing intolerance at universities in this country – not intolerance along racial or ethnic or gender lines – there, we have made laudable progress. Rather, a kind of intellectual intolerance, a political one-sidedness, that is the antithesis of what universities should stand for. It manifests itself in many ways: in the intellectual monocultures that have taken over certain disciplines; in the demands to disinvite speakers and outlaw groups whose views we find offensive; in constant calls for the university itself to take political stands. We decry certain news outlets as echo chambers, while we fail to notice the echo chamber we’ve built around ourselves.
This results in a kind of intellectual blindness that will, in the long run, be more damaging to universities than cuts in federal funding or ill-conceived constraints on immigration. It will be more damaging because we won’t even see it: We will write off those with opposing views as evil or ignorant or stupid, rather than as interlocutors worthy of consideration. We succumb to the all-purpose ad hominem because it is easier and more comforting than rational argument. But when we do, we abandon what is great about this institution we serve.
It will not be easy to resist this current. As an institution, we are continually pressed by faculty and students to take political stands, and any failure to do so is perceived as a lack of courage. But at universities today, the easiest thing to do is to succumb to that pressure. What requires real courage is to resist it. Yet when those making the demands can only imagine ignorance and stupidity on the other side, any resistance will be similarly impugned.
The university is not a megaphone to amplify this or that political view, and when it does it violates a core mission. Universities must remain open forums for contentious debate, and they cannot do so while officially espousing one side of that debate.
But we must do more. We need to encourage real diversity of thought in the professoriate, and that will be even harder to achieve. It is hard for anyone to acknowledge high-quality work when that work is at odds, perhaps opposed, to one’s own deeply held beliefs. But we all need worthy opponents to challenge us in our search for truth. It is absolutely essential to the quality of our enterprise.
I fear that the next few years will be difficult to navigate. We need to resist the external threats to our mission, but in this, we have many friends outside the university willing and able to help. But to stem or dial back our academic parochialism, we are pretty much on our own. The first step is to remind our students and colleagues that those who hold views contrary to one’s own are rarely evil or stupid, and may know or understand things that we do not. It is only when we start with this assumption that rational discourse can begin, and that the winds of freedom can blow.
Why Universities Must Choose One Telos: Truth or Social Justice
by Jonathan Haidt | Oct 21, 2016
Aristotle often evaluated a thing with respect to its “telos” – its purpose, end, or goal. The telos of a knife is to cut. The telos of a physician is health or healing. What is the telos of university?
The most obvious answer is “truth” –- the word appears on so many university crests. But increasingly, many of America’s top universities are embracing social justice as their telos, or as a second and equal telos. But can any institution or profession have two teloses (or teloi)? What happens if they conflict?
As a social psychologist who studies morality, I have watched these two teloses come into conflict increasingly often during my 30 years in the academy. The conflicts seemed manageable in the 1990s. But the intensity of conflict has grown since then, at the same time as the political diversity of the professoriate was plummeting, and at the same time as American cross-partisan hostility was rising. ...
Examples of Perverse Incentives and Replication in Science
In an earlier post (Perverse Incentives and Replication in Science), I wrote:
From a colleague at MSU:
Parts 1 and 2: Green revolution in Malawi from Farm Input Subsidy Program? Hurrah! Gushing coverage in the NYTimes, Jeffrey Sachs claiming credit, etc.
http://www.nytimes.com/2012/04/20/opinion/how-malawi-fed-its-own-people.html
http://www.nytimes.com/2007/12/02/world/africa/02malawi.html
http://www.nytimes.com/slideshow/2007/12/01/world/20071202MALAWI_index.html
Part 3: Failed replication? No actual green revolution? Will anyone notice?
For more depressing narrative concerning the reliability of published results (this time in cancer research), see this front page NYTimes story from today.
Here's a depressing but all too common pattern in scientific research:This seems to have hit a nerve, as many people have come forward with their own examples of this pattern.
1. Study reports results which reinforce the dominant, politically correct, narrative.
2. Study is widely cited in other academic work, lionized in the popular press, and used to advance real world agendas.
3. Study fails to replicate, but no one (except a few careful and independent thinkers) notices.
From a colleague at MSU:
Parts 1 and 2: Green revolution in Malawi from Farm Input Subsidy Program? Hurrah! Gushing coverage in the NYTimes, Jeffrey Sachs claiming credit, etc.
http://www.nytimes.com/2012/04/20/opinion/how-malawi-fed-its-own-people.html
http://www.nytimes.com/2007/12/02/world/africa/02malawi.html
http://www.nytimes.com/slideshow/2007/12/01/world/20071202MALAWI_index.html
Part 3: Failed replication? No actual green revolution? Will anyone notice?
Re-evaluating the Malawian Farm Input Subsidy Programme (Nature Plants)For more on the 1-2-3 pattern and replication, see this blog post by economist Douglas Campbell, and discussion here.
Joseph P. Messina1*†, Brad G. Peter1† and Sieglinde S. Snapp2†
Abstract: The Malawian Farm Input Subsidy Programme (FISP) has received praise as a proactive policy that has transformed the nation’s food security, yet irreconcilable differences exist between maize production estimates distributed by the Food and Agriculture Organization of the United Nations (FAO), the Malawi Ministry of Agriculture and Food Security (MoAFS) and the National Statistical Office (NSO) of Malawi. These differences illuminate yield-reporting deficiencies and the value that alternative, politically unbiased yield estimates could play in understanding policy impacts. We use net photosynthesis (PsnNet) as an objective source of evidence to evaluate production history and production potential under a fertilizer input scenario. Even with the most generous harvest index (HI) and area manipulation to match a reported error, we are unable to replicate post-FISP production gains. In addition, we show that the spatial delivery of FISP may have contributed to popular perception of widespread maize improvement. These triangulated lines of evidence suggest that FISP may not have been the success it was thought to be. Lastly, we assert that fertilizer subsidies may not be sufficient or sustainable strategies for production gains in Malawi.
Introduction: Input subsidies targeting agricultural production are frequent and contentious development strategies. The national scale FISP implemented in Malawi has been heralded as an ‘African green revolution’ success story1. The programme was developed by the Malawian government in response to long-term recurring food shortages, following the notably poor maize harvest of 2005; the history of FISP is well described by Chirwa and Dorward2. Scholars and press sources alike commonly refer to government statistics regarding production and yields as having improved significantly. Reaching widespread audiences, Sachs broadcasted that “production doubled within one harvest season” following its deployment3. The influential policy paper by Denning et al. opened with the statement that the “Government of Malawi implemented one of the most ambitious and successful assaults on hunger in the history of the African continent”4. The Malawi success narrative has certainly influenced global development agencies, resulting in increased support for agricultural input subsidies; Tanzania, Zambia, Kenya and Rwanda have all followed suit and implemented some form of input subsidy programme. There has been mild economic criticism of the subsidy implementation process, including disruption of private fertilizer distribution networks within the policy’s first year5. Moreover, the sustainability of subsidies in Malawi has been debated6,7, yet crop productivity gains from subsidies have gone largely unquestioned. As Sanchez commented, “in spite of criticisms by donor agencies and academics, the seed and fertilizer subsidies provided food security to millions of Malawians”1. This optimistic assessment of potential for an “African green revolution” must be tempered by the fact that the Malawian production miracle appears, in part, to be a myth. ...
For more depressing narrative concerning the reliability of published results (this time in cancer research), see this front page NYTimes story from today.
Monday, March 06, 2017
The Eyes of Texas
Sorry for the blogging interruption. I'm at the annual AAU (Association of American Universities) meeting of Senior Research Officers in Austin, Texas.
UT Austin has a beautiful clock tower just up the street from our hotel. As pretty as it is I couldn't help but think about the 1966 tower sniper (45 casualties in 96 minutes) while walking around the main quad. It's a heartbreaking story.
The Eyes of Texas are upon you,
All the live long day.
The Eyes of Texas are upon you,
You can not get away.
Do not think you can escape them
At night or early in the morn
The Eyes of Texas are upon you
'Till Gabriel blows his horn.
Subscribe to:
Posts (Atom)
Blog Archive
-
▼
2017
(149)
-
▼
03
(13)
- The brute tyranny of g-loading: Lawrence Krauss an...
- Just Like Heaven
- Robots Proctor Online Exams
- The weirdest academic seminar ever
- With Kasparov in NYC
- Nunes, Trump, Obama and Who Watches the Watchers?
- FISA, EO 12333, Bulk Collection, and All That
- Everything is Heritable
- Ginormous Neural Nets and Networks of Networks
- Dalton Conley: The Bell Curve Revisited and The Ge...
- "We need to encourage real diversity of thought in...
- Examples of Perverse Incentives and Replication in...
- The Eyes of Texas
-
▼
03
(13)
Labels
- physics (420)
- genetics (325)
- globalization (301)
- genomics (295)
- technology (282)
- brainpower (280)
- finance (275)
- american society (261)
- China (249)
- innovation (231)
- ai (206)
- economics (202)
- psychometrics (190)
- science (172)
- psychology (169)
- machine learning (166)
- biology (163)
- photos (162)
- genetic engineering (150)
- universities (150)
- travel (144)
- podcasts (143)
- higher education (141)
- startups (139)
- human capital (127)
- geopolitics (124)
- credit crisis (115)
- political correctness (108)
- iq (107)
- quantum mechanics (107)
- cognitive science (103)
- autobiographical (97)
- politics (93)
- careers (90)
- bounded rationality (88)
- social science (86)
- history of science (85)
- realpolitik (85)
- statistics (83)
- elitism (81)
- talks (80)
- evolution (79)
- credit crunch (78)
- biotech (76)
- genius (76)
- gilded age (73)
- income inequality (73)
- caltech (68)
- books (64)
- academia (62)
- history (61)
- intellectual history (61)
- MSU (60)
- sci fi (60)
- harvard (58)
- silicon valley (58)
- mma (57)
- mathematics (55)
- education (53)
- video (52)
- kids (51)
- bgi (48)
- black holes (48)
- cdo (45)
- derivatives (43)
- neuroscience (43)
- affirmative action (42)
- behavioral economics (42)
- economic history (42)
- literature (42)
- nuclear weapons (42)
- computing (41)
- jiujitsu (41)
- physical training (40)
- film (39)
- many worlds (39)
- quantum field theory (39)
- expert prediction (37)
- ufc (37)
- bjj (36)
- bubbles (36)
- mortgages (36)
- google (35)
- race relations (35)
- hedge funds (34)
- security (34)
- von Neumann (34)
- meritocracy (31)
- feynman (30)
- quants (30)
- taiwan (30)
- efficient markets (29)
- foo camp (29)
- movies (29)
- sports (29)
- music (28)
- singularity (27)
- entrepreneurs (26)
- conferences (25)
- housing (25)
- obama (25)
- subprime (25)
- venture capital (25)
- berkeley (24)
- epidemics (24)
- war (24)
- wall street (23)
- athletics (22)
- russia (22)
- ultimate fighting (22)
- cds (20)
- internet (20)
- new yorker (20)
- blogging (19)
- japan (19)
- scifoo (19)
- christmas (18)
- dna (18)
- gender (18)
- goldman sachs (18)
- university of oregon (18)
- cold war (17)
- cryptography (17)
- freeman dyson (17)
- smpy (17)
- treasury bailout (17)
- algorithms (16)
- autism (16)
- personality (16)
- privacy (16)
- Fermi problems (15)
- cosmology (15)
- happiness (15)
- height (15)
- india (15)
- oppenheimer (15)
- probability (15)
- social networks (15)
- wwii (15)
- fitness (14)
- government (14)
- les grandes ecoles (14)
- neanderthals (14)
- quantum computers (14)
- blade runner (13)
- chess (13)
- hedonic treadmill (13)
- nsa (13)
- philosophy of mind (13)
- research (13)
- aspergers (12)
- climate change (12)
- harvard society of fellows (12)
- malcolm gladwell (12)
- net worth (12)
- nobel prize (12)
- pseudoscience (12)
- Einstein (11)
- art (11)
- democracy (11)
- entropy (11)
- geeks (11)
- string theory (11)
- television (11)
- Go (10)
- ability (10)
- complexity (10)
- dating (10)
- energy (10)
- football (10)
- france (10)
- italy (10)
- mutants (10)
- nerds (10)
- olympics (10)
- pop culture (10)
- crossfit (9)
- encryption (9)
- eugene (9)
- flynn effect (9)
- james salter (9)
- simulation (9)
- tail risk (9)
- turing test (9)
- alan turing (8)
- alpha (8)
- ashkenazim (8)
- data mining (8)
- determinism (8)
- environmentalism (8)
- games (8)
- keynes (8)
- manhattan (8)
- new york times (8)
- pca (8)
- philip k. dick (8)
- qcd (8)
- real estate (8)
- robot genius (8)
- success (8)
- usain bolt (8)
- Iran (7)
- aig (7)
- basketball (7)
- free will (7)
- fx (7)
- game theory (7)
- hugh everett (7)
- inequality (7)
- information theory (7)
- iraq war (7)
- markets (7)
- paris (7)
- patents (7)
- poker (7)
- teaching (7)
- vietnam war (7)
- volatility (7)
- anthropic principle (6)
- bayes (6)
- class (6)
- drones (6)
- econtalk (6)
- empire (6)
- global warming (6)
- godel (6)
- intellectual property (6)
- nassim taleb (6)
- noam chomsky (6)
- prostitution (6)
- rationality (6)
- academia sinica (5)
- bobby fischer (5)
- demographics (5)
- fake alpha (5)
- kasparov (5)
- luck (5)
- nonlinearity (5)
- perimeter institute (5)
- renaissance technologies (5)
- sad but true (5)
- software development (5)
- solar energy (5)
- warren buffet (5)
- 100m (4)
- Poincare (4)
- assortative mating (4)
- bill gates (4)
- borges (4)
- cambridge uk (4)
- censorship (4)
- charles darwin (4)
- computers (4)
- creativity (4)
- hormones (4)
- humor (4)
- judo (4)
- kerviel (4)
- microsoft (4)
- mixed martial arts (4)
- monsters (4)
- moore's law (4)
- soros (4)
- supercomputers (4)
- trento (4)
- 200m (3)
- babies (3)
- brain drain (3)
- charlie munger (3)
- cheng ting hsu (3)
- chet baker (3)
- correlation (3)
- ecosystems (3)
- equity risk premium (3)
- facebook (3)
- fannie (3)
- feminism (3)
- fst (3)
- intellectual ventures (3)
- jim simons (3)
- language (3)
- lee kwan yew (3)
- lewontin fallacy (3)
- lhc (3)
- magic (3)
- michael lewis (3)
- mit (3)
- nathan myhrvold (3)
- neal stephenson (3)
- olympiads (3)
- path integrals (3)
- risk preference (3)
- search (3)
- sec (3)
- sivs (3)
- society generale (3)
- systemic risk (3)
- thailand (3)
- twitter (3)
- alibaba (2)
- bear stearns (2)
- bruce springsteen (2)
- charles babbage (2)
- cloning (2)
- david mamet (2)
- digital books (2)
- donald mackenzie (2)
- drugs (2)
- dune (2)
- exchange rates (2)
- frauds (2)
- freddie (2)
- gaussian copula (2)
- heinlein (2)
- industrial revolution (2)
- james watson (2)
- ltcm (2)
- mating (2)
- mba (2)
- mccain (2)
- monkeys (2)
- national character (2)
- nicholas metropolis (2)
- no holds barred (2)
- offices (2)
- oligarchs (2)
- palin (2)
- population structure (2)
- prisoner's dilemma (2)
- singapore (2)
- skidelsky (2)
- socgen (2)
- sprints (2)
- star wars (2)
- ussr (2)
- variance (2)
- virtual reality (2)
- war nerd (2)
- abx (1)
- anathem (1)
- andrew lo (1)
- antikythera mechanism (1)
- athens (1)
- atlas shrugged (1)
- ayn rand (1)
- bay area (1)
- beats (1)
- book search (1)
- bunnie huang (1)
- car dealers (1)
- carlos slim (1)
- catastrophe bonds (1)
- cdos (1)
- ces 2008 (1)
- chance (1)
- children (1)
- cochran-harpending (1)
- cpi (1)
- david x. li (1)
- dick cavett (1)
- dolomites (1)
- eharmony (1)
- eliot spitzer (1)
- escorts (1)
- faces (1)
- fads (1)
- favorite posts (1)
- fiber optic cable (1)
- francis crick (1)
- gary brecher (1)
- gizmos (1)
- greece (1)
- greenspan (1)
- hypocrisy (1)
- igon value (1)
- iit (1)
- inflation (1)
- information asymmetry (1)
- iphone (1)
- jack kerouac (1)
- jaynes (1)
- jazz (1)
- jfk (1)
- john dolan (1)
- john kerry (1)
- john paulson (1)
- john searle (1)
- john tierney (1)
- jonathan littell (1)
- las vegas (1)
- lawyers (1)
- lehman auction (1)
- les bienveillantes (1)
- lowell wood (1)
- lse (1)
- machine (1)
- mcgeorge bundy (1)
- mexico (1)
- michael jackson (1)
- mickey rourke (1)
- migration (1)
- money:tech (1)
- myron scholes (1)
- netwon institute (1)
- networks (1)
- newton institute (1)
- nfl (1)
- oliver stone (1)
- phil gramm (1)
- philanthropy (1)
- philip greenspun (1)
- portfolio theory (1)
- power laws (1)
- pyschology (1)
- randomness (1)
- recession (1)
- sales (1)
- skype (1)
- standard deviation (1)
- starship troopers (1)
- students today (1)
- teleportation (1)
- tierney lab blog (1)
- tomonaga (1)
- tyler cowen (1)
- venice (1)
- violence (1)
- virtual meetings (1)
- wealth effect (1)